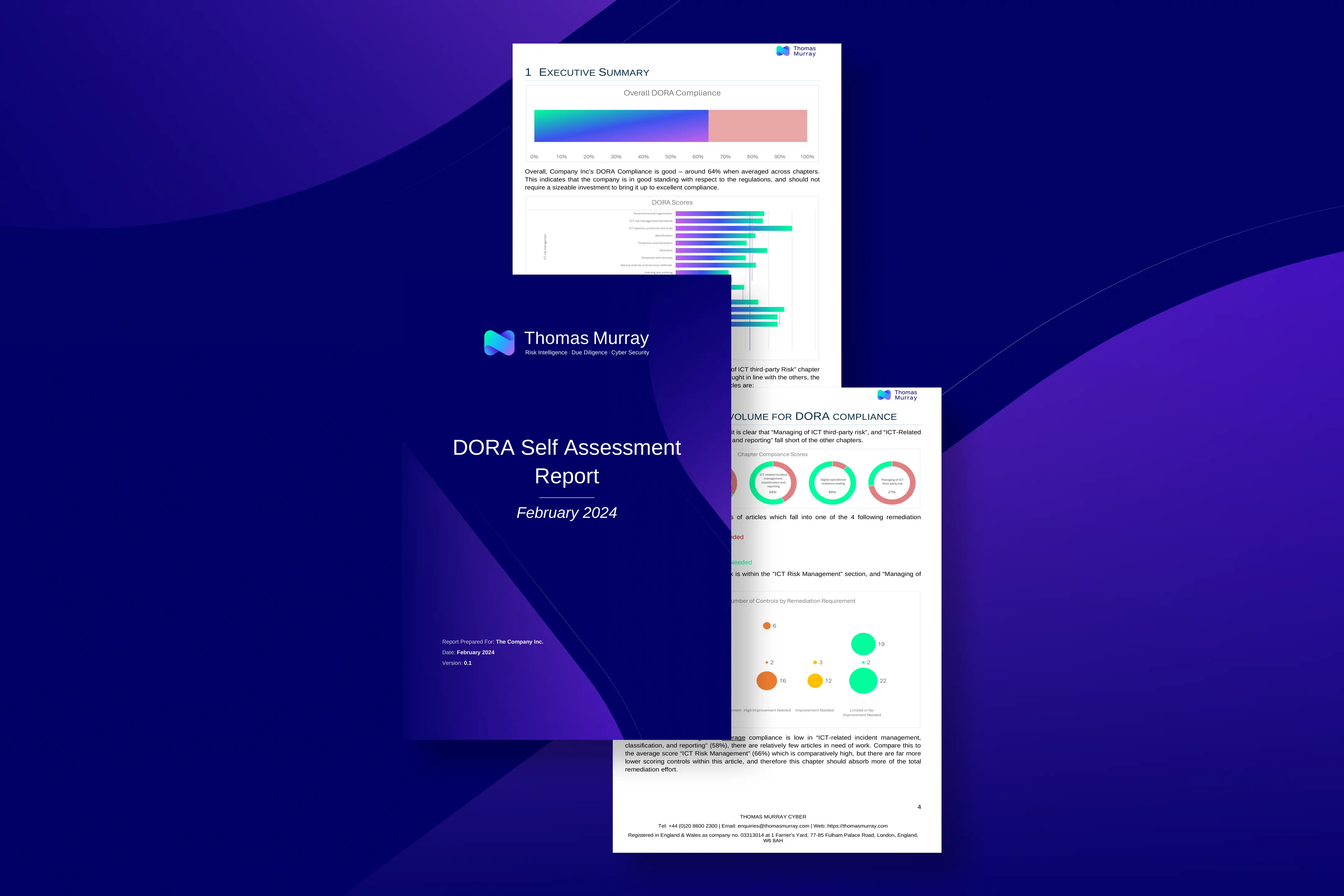
The Digital Operational Resilience Act (DORA) is a new EU financial regulation that will take effect from 17 January 2025.
The aim of DORA is to address the fact that information and communication technology (ICT) incidents and a lack of operational resilience carry the risk of jeopardising the soundness of the entire financial system, even if there are “adequate” measures in place to mitigate so-called traditional risks.
Spitz Poulle Kannan provides advice exclusively on financial services and regulations. Based in Paris, the firm mainly assists French and international banks, investment firms, portfolio managers and insurance companies. SPK also works with more than 20 preferred law firms across multiple jurisdictions, with a view to offering seamless cross-border advice to its clients.
Lise Wantier is an Associate at Spitz Poulle Kannan. She advises credit institutions, investment and management companies, payment institutions, market infrastructures, fintechs and custodians on their organisation and regulatory frameworks. She also intervenes in litigation matters.


About the author
Christine Young
Managing Consultant | Advisory
Christine Young joined Thomas Murray’s Advisory team in 2022, after 30 years in the asset servicing sector. Her previous role was at BNY Mellon, where Christine was responsible for the risk and regulatory control function in the asset servicing business, having led the development of the control framework for the business. She has also held roles in sales, corporate development and relationship management. Christine has both legal and accounting qualifications, and extensive experience in working on multi-discipline projects in global jurisdictions.
Christine Young: How does DORA fit into the existing regulatory landscape in terms of technology risk?
Spitz Poulle Kannan: “The financial sector has become as much about data and technology as it is about money and capital.” This is one of the key findings of the impact assessment on the DORA proposal (Impact Assessment).
The use of information and communication technology (ICT) has scaled up significantly in the last few decades and it now has a pivotal role in the financial sector. However, ICT has also created risks and vulnerabilities, as financial entities are increasingly exposed to cyber attacks or incidents. In 2019, the Boston Consulting Group found that firms operating in the financial services industry were 300 times more likely than other companies to be the target of cyber attacks.
While EU laws covered at length the main categories of financial risks (for example, credit risk, market risk, counterparty credit risk and liquidity risk, market conduct risk), they did not initially cover all components of ICT risks.
As a result, ICT risks were addressed in a piecemeal fashion through various EU and national laws and not all sectors were covered equally – as highlighted in recital 10 of DORA:
“There are gaps or overlaps in important areas, such as ICT-related incident reporting and digital operational resilience testing, and inconsistencies as a result of emerging divergent national rules or cost-ineffective application of overlapping rules. This is particularly detrimental for an ICT-intensive user such as the financial sector since technology risks have no borders and the financial sector deploys its services on a wide cross-border basis within and outside the [European] Union.”
For example, the disparate manner in which ICT risks are currently covered in France is the cumulative application of several rules and guidelines. These include the European Banking Authority (EBA) guidelines on outsourcing arrangements, ICT and security risk management and internal governance, and the Order of 3 November 2014 on internal control providing rules regarding governance and organisation of internal control, outsourcing and ICT risk management.
It's worth noting that the French banking authority (Autorité de contrôle prudentiel et de resolution (ACPR)) had also published a notice on IT risk management (ACPR, Notice relative à la gestion du risque informatique pour les entreprises du secteur de la banque, des services de paiement et des services d'investissement, 7 July 2021).
In short, there is a regulatory framework covering ICT risks in place in the EU, but this framework is patchy, uncoordinated, and incomplete.
The aim of DORA is to provide harmonised requirements: the rules laid down by DORA will supersede all those already in place for the financial sector in scattered regulations, be they EU or national regulations.
There is a legal doctrine of ‘lex specialis’, which basically means that if two laws govern the same factual situation, the law that governs a specific subject matter (lex specialis) will override the one governing only general matters (lex generalis).
We mention this doctrine because of the NIS II directive on measures for a high common level of cybersecurity across the EU. DORA builds on NIS II, and is ‘lex specialis’ to it as far as the financial sector is concerned. There are two reasons for this:
- Firstly, the importance of ICT to the sector. Finance is the largest ICT user in the world, and accounts for about 20% of all total ICT expenditure.
- Secondly, ICT risks are a source of systemic risk. For example, in the case of cyber attacks, ICT risks can spread more quickly and at a larger scale across sectors and beyond geographical borders, triggering liquidity runs and an overall loss of confidence and trust in financial markets.
This approach seems to have been welcomed by the market during the consultation process. In the Impact Assessment, it’s noted that:
“Most stakeholders (private, public) agree that EU action is needed to better safeguard financial firms’ operational resilience. Many also believe that EU action is necessary to address the regulatory burdens stemming from financial firms being subject to duplicative and inconsistent rules set out in NIS, EU financial services law and national regimes (e.g. as regards incident reporting).”
CY: Are there any areas that lack clarity ahead of the consultations regarding technical standards, both regulatory and implementing?
SPK: DORA states that the European Supervisory Authorities (the ESAs) are mandated to jointly develop policy instruments. In this respect:
- regulatory technical standards (RTS) will be drafted in the areas of ICT risk management, major ICT-related incident reporting, testing, as well as in relation to key requirements for a sound monitoring of ICT third-party risk; and
- implementing technical standards (ITS) will be drafted to establish standardised templates, forms and procedures for financial entities to report a major ICT-related incident and a major operational or security payment-related incident, as well as standardised templates for the register of information.
Delegated acts are also envisaged in DORA. The European Commission has already requested the technical advice of ESAs to assist on the content of these delegated acts.
RTS, ITS and delegated acts can have a major impact, even though they do not involve policy choices, since they are only intended to (i) specify and (ii) adapt (in accordance with the principle of proportionality) general rules already contained in DORA.
In the case at hand, a delegated act will specify the criteria to determine ICT third-party service providers that are critical for financial entities. A designation of critical third-party service provider (CTPP) status will subject the entity to a new oversight framework.
The way in which these criteria will be specified is therefore crucial, and may determine if certain actors will be considered as CTPPs. If the criteria are not clear enough, there is a risk of uncertainty for both the ICT service providers and for financial entities. This would especially be the case if it is not known which ICT providers will be captured by the oversight framework under DORA. As a result, it will be very challenging for financial institutions and ICT service providers to plan for their cyber strategy, investments and/or legal entity’s structure.
Finally, the interplay between DORA and the EBA Guidelines on Outsourcing may also give rise to certain other issues.
CY: How will regulators respond?
SPK: EU and national regulators have a key role in the successful application of DORA. To understand how regulators will respond, it is necessary to recall that:
A. the ESAs will be on the front line to supervise CTPPs, and
B. national competent authorities will remain responsible for ensuring that the financial entities placed under their supervision comply with their obligations.
A. The ESA’s supervision of CTPPs
DORA is setting a new EU precedent by bringing CTPPs into direct oversight of the ESAs. In practice, supervision will be organised as follows:
- An ICT service provider, considered as critical to the stability and integrity of the EU financial system, will be designated as a CTPP by the ESAs through a Joint Committee.
- Then, a Lead Overseer will be appointed for each CTPP among the ESAs. Depending on whether the CTPP provides most of its services to banking, financial or insurance entities, the responsible ESA will be either the EBA, the European Securities and Markets Authority, or the European Insurance and Occupational Pensions Authority.
- The Lead Overseer will be:
- responsible for the direct supervision of the CTPP. The authority will have the power to monitor on a pan-European scale the CTPP’s activities, by requesting information, carrying out investigations and general inspections, making recommendations, and issuing warnings or imposing fines; and
- assisted by a “joint examination team.” This team will be made up of staff members from the competent national authorities that are supervising the financial entities to which the CTPP provides its ICT services.
This supervision involves costs, which have been anticipated by the ESAs. In the Impact Assessment it says:
“Over the last few years, several prudential supervisors have been increasing their resources dedicated to IT supervision. … For supervisors: the current costs for supervisory authorities associated to ICT supervision are between 5% and 10% of the total IT supervision staff. … a marginal increase in FTEs could be expected, due to the additional tasks supervisors would have to deal with (e.g. including additional reporting of incidents).”
B. The supervision of financial entities by national authorities
Financial entities:
(i) must report major ICT-related incidents; and
(ii) may voluntarily report significant cyber threats to their national competent authorities.
For significant credit institutions, national authorities will have to forward this notification to the European Central Bank (ECB) immediately.
In France, the French banking authority (the ACPR) already has governance, cyber risk and systemic risk teams within its departments. Cyber risk has been an inspection priority for years, and the ACPR was already carrying out assessments to identify breaches of information security by financial institutions. Similarly, the French financial market authority (Autorité des marchés financiers (the AMF)) already has a digital finance and innovation team.
In anticipation of DORA taking effect, the ACPR and the AMF have started to focus on recruiting.
For example, the ACPR is recruiting information systems controllers, who will audit the information systems of financial institutions, with a focus on their robustness and security. Meanwhile, the AMF is recruiting for a ‘digital asset service provider supervisor’, specialising in cybersecurity and information systems.
CY: Do you expect DORA to uncover systemic vulnerabilities in Europe, for example to a handful of common IT service providers?
SPK: In 2020, the European Systemic Risk Board and the Financial Stability Board stressed that the existing high level of interconnectedness across financial entities’ ICT systems could constitute a systemic vulnerability, with the potential to have serious negative consequences for the real economy.
DORA’s preparatory work, based on these reports, highlighted that these vulnerabilities are caused in particular by:
- One, the increased outsourcing practices and the ICT third-party concentration; and
- Two, the insufficiency of national mechanisms in providing financial supervisors with adequate tools to quantify, qualify and redress the consequences of ICT risk occurring at ICT third-party providers.
The Impact Assessment highlights that:
“A global consensus among authorities has formed that ICT risks are a source of systemic risk in the financial sector. Recent studies and papers published in Europe and in the US demonstrate that ICT risk can threaten the stability of the entire financial system and that this type of risk can itself trigger a liquidity crisis and be a source of systemic risk.”
DORA offers a wide range of measures to deal with the risks identified. A first set of measures focuses on financial entities by:
(i) strengthening their ICT capabilities and overall resilience, and
(ii) providing sufficient safeguards for the fully-fledged monitoring of subcontracting processes with CTPPs (financial entities often encounter difficulties in negotiating contractual terms, or in enforcing specific rights, such as access or audit rights).
A second set of measures focuses on CTPPs by establishing an oversight framework to monitor their activities. These measures will give financial entities and regulators more tools for identifying and assessing ICT risks.
By 17 January 2028, the Commission shall carry out a review of the different tools and measures provided by DORA, and submit a report to the European Parliament and the Council. Where appropriate, this will be accompanied by a legislative proposal. If systemic vulnerabilities are uncovered, it will probably lead to a second version of DORA (under the “do it and fix it” approach).
Finally, one of the underlying issues in the preparatory work for DORA is the dependence regarding non-EU actors. This dependence generates vulnerability for EU financial entities, and cannot be resolved exclusively from a legal standpoint. The Impact Assessment points out that, “ICT TPP oversight may not eliminate concentration risks given that the ICT TTPs market is currently dominated by four large players, all of them non-European.”
As EU authorities have grown increasingly sensitive to this issue, technical projects are underway to address it – such as Gaia-X, which is an EU initiative that aims to develop an efficient, competitive and secure cloud computing offering for the EU. According to the chief digital and information officer of Elior Group, “Europe’s digital sovereignty is closely linked to its ability to control its dependence on the cloud market, in particular by developing trusted cloud services.”
CY: Do you think that DORA will enhance the cyber resilience of the EU financial services ecosystem?
SPK: As we mentioned, firms operating in the financial services industry are 300 times more likely than other companies to be the target of cyber attacks. In the case of cyber attacks, ICT risks can spread more quickly and at a larger scale, across sectors and beyond geographical borders, triggering liquidity runs and an overall loss of confidence and trust in financial markets.
Cyber resilience is defined by the ECB as, “the ability to protect electronic data and systems from cyberattacks, as well as to resume business operations quickly in case of a successful attack.”
Cyber resilience can be improved by acting on two key factors:
(i) the ability to protect electronic data and systems from cyber attacks – that is, avoid cyber attack; and
(ii) if the cyber attack cannot be avoided, the capacity to resume business operations quickly.
In our view, DORA will enhance the cyber resilience of the EU financial services ecosystem by acting on the two key elements.
Firstly, DORA includes a wide range of measures regarding the ability to protect electronic data and systems from cyber attacks, for example by introducing requirements around:
- risk identification (mapping);
- ICT risk management and ICT-related incident reporting; and
- information-sharing mechanisms (contributing to increased awareness of cyber threats) or digital resilience testing.
Secondly, DORA includes measures regarding the capacity of financial institutions to resume business operations quickly when a cyber attack cannot be avoided. For example, financial entities will be required to have cyber attack and failover to redundant infrastructure scenarios in their business continuity plans, or a crisis communication plan.
A final point here is that DORA favoured qualitative rules (for the protection, detection, containment, recovery and repair capabilities against ICT-related incidents, or for reporting and digital testing capabilities). We believe these will complete efficiently the traditional quantitative approach to addressing risk (namely, setting a capital requirement to cover ICT risk).
CY: Do you foresee any unintended consequences to DORA? For example, could it create more concentration risk as EU financial institutions choose to use EU-based IT service providers?
SPK: Legislators have been attentive to the market feedback regarding the impact of DORA. For example, to reduce concentration risk, DORA provides that financial entities must adopt an ICT multi-vendor strategy (to avoid dependency on a single or a few ICT vendors).
The European Banking Federation (EBF) has noted that where 3-5 large vendors dominate an entire sector, an ICT multi-vendor strategy will not reduce concentration risk systemically. Instead, there is a risk of adding cost and complexity for financial entities. The EBF has stated that:
“The innovative capabilities technology vendors offer are most often vendor-specific – so they cannot be ‘rotated’, meaning the EU financial sector may lose access to state-of-the-art technology solutions. This can harm the competitiveness of the EU financial sector without reducing the concentration risk, entailing considerable cost for little benefit. Also, when applied to an EU legal entity within a group structure, the requirement could force the firm to shift from relying on an intra-group arrangement to depend on an external technology provider, increasing the concentration risk that the Regulation aims to reduce.”
These concerns have been heard; in the final version of DORA the wording has been amended. For example, Article 6(9) of DORA now says that entities “may” (rather than “must”) define a holistic ICT multi-vendor strategy.
One of the main concerns today in relation to DORA’s implementation relates to the supervision of CTPPs. The risk identified (in particular by Google Cloud and the American Chamber of Commerce to the EU) is that the lead overseer will be able to monitor all the services provided by a CTPP, including those which are not used by financial entities for critical and important functions.
It could be that supervisory effectiveness will be reduced as more resources are applied to services that have minimal or no impact on digital operational resilience.
Regarding the concentration risk with non-EU players, this issue was clearly identified in the preparatory work for DORA. To limit this risk, DORA has introduced rules to supervise CTPPs and to ensure their supervision. DORA provides in Article 31(12) that: “Financial entities shall only make use of the services of [a CTPP] … if the latter has established a subsidiary in the Union within the 12 months following the designation.”
You might ask whether this new regulatory framework will lead to the withdrawal of non-EU CTPPs from the EU market as they seek to avoid regulatory burdens. On this point, we note that:
- the European market is too important for these entities to withdraw from – they did not, for example, stop providing services in the EU when the EBA introduced its guidelines on outsourcing; and
- most of the entities that will qualify as CTPPs already have a subsidiary in the EU, and therefore seemed to have anticipated the new requirements.
CY: Do you think it is likely that both regulators and financial institutions will be ready by January 2025?
SPK: DORA consolidates and upgrades ICT risk requirements that have, up to this point, only been addressed disparately in various EU laws. Therefore, for some entities that fall within the scope of DORA, implementing the new regulatory framework will be an additional brick in their compliance process.
It is worth mentioning that major French banks have already launched DORA compliance projects. Our law firm is already in the process of assisting these banks regarding the interplay between the EBA outsourcing guidelines and DORA, and the amendments that will need to be introduced in the relevant contractual documentation.
However, there is a real challenge for the smallest entities and entities that until now were not subject to most of the requirements. These entities are also more likely to have fewer resources to carry out the work, and cannot swiftly deploy funds to develop governance structures and set up various corporate strategies.
The publication schedule for DORA’s RTS/ITS may not give financial entities much time to comply. DORA will apply from 17 January 2025, and the finalisation of the RTS/ITS is scheduled for 17 January 2024 (first batch) and 17 June 2024 (second batch). This may raise concerns, as some RTS are crucial for a fuller understanding of DORA’s requirements of firms.
For the American Chamber of Commerce to the EU, “It is highly unlikely that financial entities will be able to safely make such technical changes in the timelines allowed. Therefore, national competent authorities should be prepared to grant allowances to the firms they supervise.”
To date, we have not noticed any indication of tolerance from the supervisors on the timelines. Regulators in general have been trying to prepare the financial entities for DORA. The ACPR has stated that, “to anticipate DORA, strengthening current governance is the best preparation.”
This article is not to be treated as legal advice.
Are you ready for DORA?
Use our free, easy-to-follow Readiness Toolkit to determine how close your organisation is to meeting all the Digital Operational Resilience Act (DORA) requirements. Once completed, we’ll send you a free report outlining how prepared you are for DORA. You can use our output to create an action plan to achieve compliance by 17 January 2025.